Download Performing CyberOps Using Cisco Security Technologies.350-201.ExamTopics.2025-07-31.137q.vcex
| Vendor: | Cisco |
| Exam Code: | 350-201 |
| Exam Name: | Performing CyberOps Using Cisco Security Technologies |
| Date: | Jul 31, 2025 |
| File Size: | 9 MB |
| Downloads: | 6 |
How to open VCEX files?
Files with VCEX extension can be opened by ProfExam Simulator.
Discount: 20%
Demo Questions
Question 1
Drag and drop the components from the left onto the phases of the CI/CD pipeline on the right.
Correct answer: To work with this question, an Exam Simulator is required.
Explanation:
Reference:https://www.densify.com/resources/continuous-integration-delivery-phases Reference:
https://www.densify.com/resources/continuous-integration-delivery-phases
Question 2
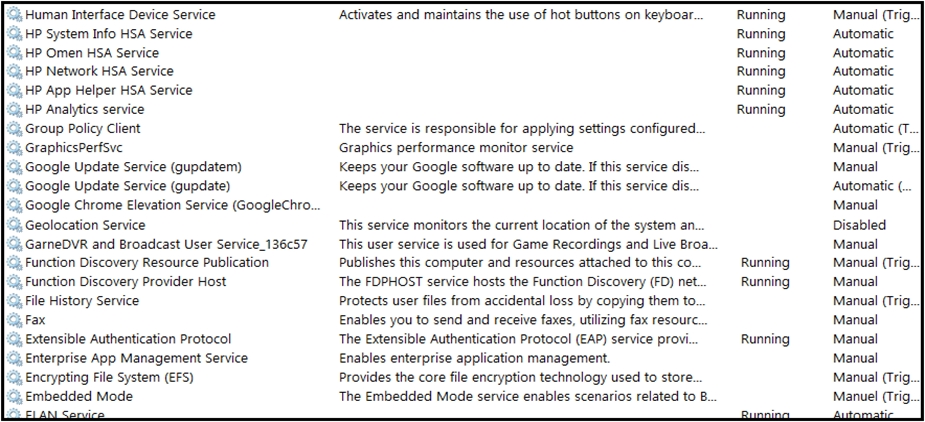
Refer to the exhibit. An engineer received multiple reports from employees unable to log into systems with the error: The Group Policy Client service failed to logon `" Access is denied. Through further analysis, the engineer discovered several unexpected modifications to system settings. Which type of breach is occurring?
- malware break
- data theft
- elevation of privileges
- denial-of-service
Correct answer: C
Question 3
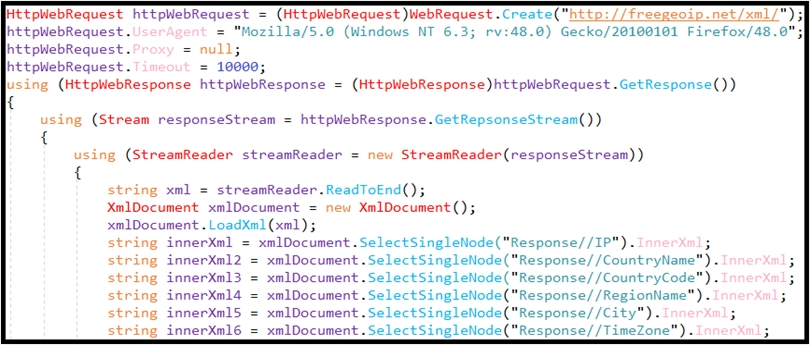
Refer to the exhibit. An engineer is performing static analysis of a file received and reported by a user. Which risk is indicated in this STIX?
- The file is redirecting users to a website that requests privilege escalations from the user.
- The file is redirecting users to the website that is downloading ransomware to encrypt files.
- The file is redirecting users to a website that harvests cookies and stored account information.
- The file is redirecting users to a website that is determining users' geographic location.
Correct answer: D
Explanation:
B: 1D: 1 B: 1D: 1
Question 4
An engineer is developing an application that requires frequent updates to close feedback loops and enable teams to quickly apply patches. The team wants their code updates to get to market as often as possible. Which software development approach should be used to accomplish these goals?
- continuous delivery
- continuous integration
- continuous deployment
- continuous monitoring
Correct answer: A
Explanation:
A: 1 A: 1
Question 5
A SOC analyst detected a ransomware outbreak in the organization coming from a malicious email attachment. Affected parties are notified, and the incident response team is assigned to the case. According to the NIST incident response handbook, what is the next step in handling the incident?
- Create a follow-up report based on the incident documentation.
- Perform a vulnerability assessment to find existing vulnerabilities.
- Eradicate malicious software from the infected machines.
- Collect evidence and maintain a chain-of-custody during further analysis.
Correct answer: D
Explanation:
C: 1 C: 1
Question 6
What is the impact of hardening machine images for deployment?
- reduces the attack surface
- increases the speed of patch deployment
- reduces the steps needed to mitigate threats
- increases the availability of threat alerts
Correct answer: A
Explanation:
A: 1 A: 1
Question 7
An audit is assessing a small business that is selling automotive parts and diagnostic services. Due to increased customer demands, the company recently started to accept credit card payments and acquired a POS terminal. Which compliance regulations must the audit apply to the company?
- HIPAA
- FISMA
- COBIT
- PCI DSS
Correct answer: D
Explanation:
D: 1Reference:https://upserve.com/restaurant-insider/restaurant-pos-pci-compliance-checklist/ D: 1
Reference:
https://upserve.com/restaurant-insider/restaurant-pos-pci-compliance-checklist/
Question 8
Refer to the exhibit. Which asset has the highest risk value?
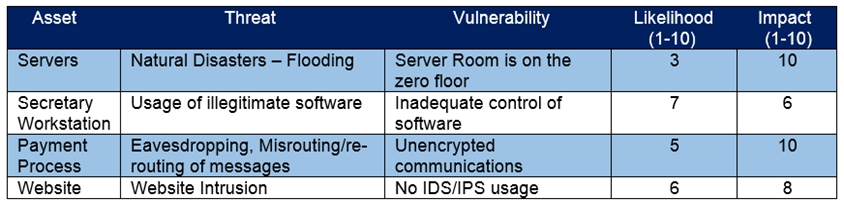
- servers
- website
- payment process
- secretary workstation
Correct answer: C
Explanation:
C: 1 C: 1
Question 9
Refer to the exhibit. What is occurring in this packet capture?
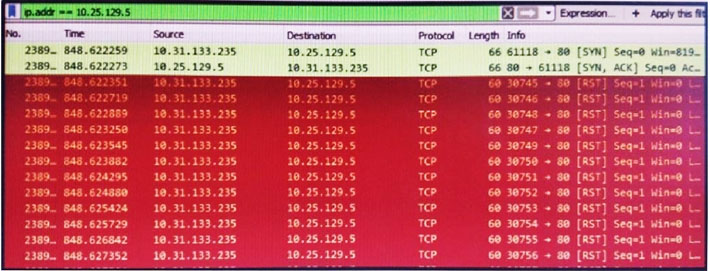
- TCP port scan
- TCP flood
- DNS flood
- DNS tunneling
Correct answer: B
Explanation:
B: 1 B: 1
Question 10
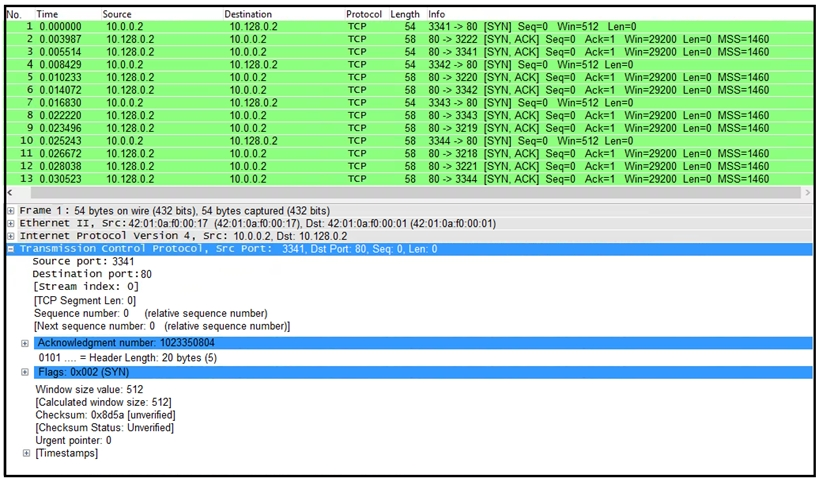
Refer to the exhibit. What is the threat in this Wireshark traffic capture?
- A high rate of SYN packets being sent from multiple sources toward a single destination IP
- A flood of ACK packets coming from a single source IP to multiple destination IPs
- A high rate of SYN packets being sent from a single source IP toward multiple destination IPs
- A flood of SYN packets coming from a single source IP to a single destination IP
Correct answer: D
Explanation:
D: 1 D: 1
Question 11
A Mac laptop user notices that several files have disappeared from their laptop documents folder. While looking for the files, the user notices that the browser history was recently cleared. The user raises a case, and an analyst reviews the network usage and discovers that it is abnormally high. Which step should be taken to continue the investigation?
- Run the sudo sysdiagnose command
- Run the sh command
- Run the w command
- Run the who command
Correct answer: A
Explanation:
A: 1Reference:https://eclecticlight.co/2016/02/06/the-ultimate-diagnostic-tool-sysdiagnose/ A: 1
Reference:
https://eclecticlight.co/2016/02/06/the-ultimate-diagnostic-tool-sysdiagnose/
HOW TO OPEN VCE FILES
Use VCE Exam Simulator to open VCE files

HOW TO OPEN VCEX AND EXAM FILES
Use ProfExam Simulator to open VCEX and EXAM files


ProfExam at a 20% markdown
You have the opportunity to purchase ProfExam at a 20% reduced price
Get Now!




